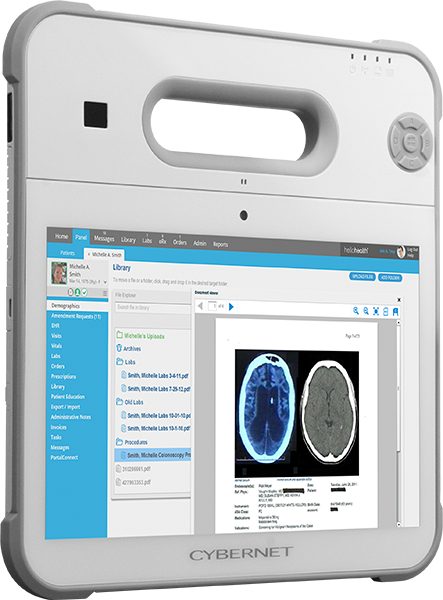
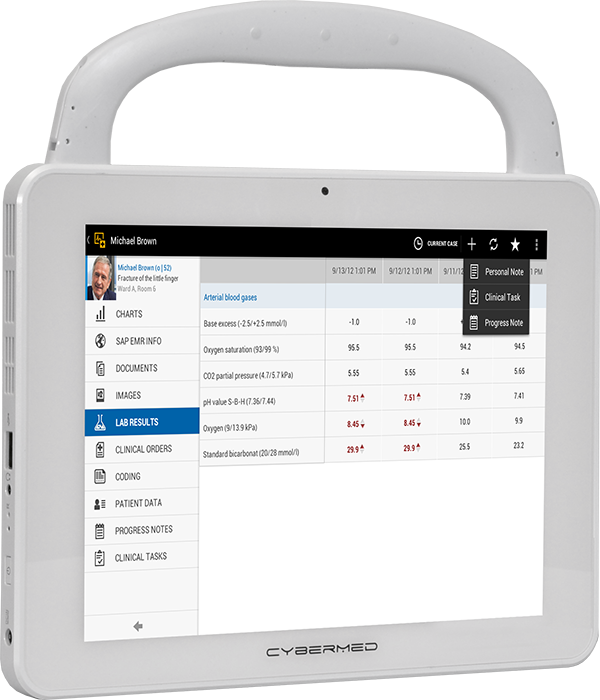
Hospitals need a lightweight electronic device for tasks like charting, electronic health records access, and remote monitoring. Medical-grade computers can solve these tasks but are too heavy and bulky to carry around comfortably all day. Smaller devices like PDAs and smartphones could handle some of these duties but aren't made to the specifications that a healthcare environment requires. So what's the solution?
The solution is a medical-grade tablet. Tablet computers have the benefit of being lighter and more portable than conventional PCs while still having greater functionality than smaller devices.
What Is a Medical-Grade Tablet?
A medical-grade tablet is a specialized and purpose-built tablet device manufactured for use in the healthcare sector. This means these tablets are distinct from consumer-grade tablets due to their unique features, specifications, and regulatory standards that they must meet before they can be used in a healthcare environment.
Medical-grade tablets are equipped with features and add-ons that streamline workflow and facilitate tasks for healthcare workers, such as RFID readers or barcode scanners. When properly used, a medical-grade tablet makes work easier and safer for doctors and nurses and provides a better patient care experience.
Learn more: Medical Grade Explained
Key Characteristics of Medical-Grade Tablets
The healthcare world demands exceptionally high standards for any piece of equipment, and medical-grade tablets are no different. Here are just a few ways these electronics are designed for their working environment.
Regulatory Compliance
The first and most important consideration for any medical electronic device is meeting the IEC 60601-1 and 60601-1-2 regulatory standards. These standards must be met for the device to be considered safe to be used around patients. IEC 60601-1 governs protection against electrical shorts, while IEC 60601-2 ensures that medical devices do not disrupt or get disrupted by other devices operating nearby.
Data security is also a significant concern for the healthcare industry. Any device that stores EHRs or patient information must meet HIPAA data privacy regulations.
Power and Storage
Medical-grade tablets will have to access a considerable amount of data, such as patient records, diagnostic images, prescription information, and more. This means they will need lots of storage space to save this data, with 128 to 500 GB being the recommended amount.
Despite their size, tablets must also be capable of running multiple applications without freezing or slowing down. A medical-grade tablet's processor should be in the range of 1.9 to 3.2 GHz and have at least 8 GB of memory to run Windows operating systems in 64-bit mode.
Ruggedness and Durability
Sadly, most electronics do not have a reputation for being sturdy. This is something a hospital cannot afford. For this reason, medical tablets should be ruggedized to withstand drops and physical impacts during regular use and continue functioning.
Another important consideration is water and dust. Dust is an enemy of electronics everywhere and can cause performance slowdowns and permanent damage if it gets into the device. Similarly, water or any liquid found in a healthcare environment, such as blood, saliva, or disinfectant, can also permanently damage electronics if it leaks through the casing. Enter IP65 rating: An ingress protection rating that indicates that the device is both dustproof and waterproof.
User-Friendliness
The user experience is critical for any device. When it comes to medical-grade tablets, striking a balance between power and durability while ensuring comfort during extended use by healthcare workers becomes paramount. This balance requires the medical tablet to be both lightweight and ergonomic.
Minimizing training time is also a key concern. To achieve this, medical-grade tablets offer intuitive features like touch screens and styluses. These tools simplify navigation through applications, facilitate electronic document signing, and make prescription writing a breeze.
Key Features of Medical Tablets
Along with their construction, a crucial part of what is a medical-grade tablet is its features that separate from normal consumer devices. These features include:
- RFID readers: These are used to control who can access the tablet, ensuring that only staff with the proper RFID tag can use the device.
- Barcode scanners: These can scan a patient's wristband or medication bottle's label, allowing staff to quickly identify and pull up the correct records for the patient or medication.
- Multiple ports: Healthcare facilities often use legacy equipment that relies on older types of connectors no longer in common use. A medical-grade tablet will feature legacy ports that allow it to connect with these devices.
- Multiple processor options: Medical tablets often feature multiple choices for processors, which offer different balances between processing power and battery life. Some end-users will want as much processing power as possible, while others will prioritize longevity instead.
Common Applications & Uses of Medical Tablets
Thanks to their portability and ease of use, medical-grade tablets have been implemented in numerous roles that used to be paper-based. Some of these uses include:
- Electronic health records access: With a tablet, a doctor or nurse can quickly look up a patient's medical history, diagnoses, treatment plans, and more. This saves them time from referencing the physical version of those records, which may be stored elsewhere. It also ensures that only authorized personnel can view those files.
- Medication administration: A medical tablet's built-in barcode scanner helps ensure patients are administered the right medicine at the right time. Scanning the bottle before administering the dosage logs when the medicine was issued, and by whom for the sake of recordkeeping.
- Telemedicine and remote monitoring: Because tablets are portable, patients can take them home with them when they leave the hospital but still require a degree of monitoring by medical staff. This gives hospital staff a secure and reliable way of staying in touch with the patient and saves the patient a trip to the hospital if they want to reach out to their doctor.
- Patient kiosks: A tablet can be permanently mounted on a wall or booth to serve as a patient kiosk. These set-ups allow patients to check in at a hospital, enter their personal and insurance information, and make co-payments without speaking to the hospital's staff. This lets those staff members focus on other tasks and reduces exposure if the patient has a contagious condition.
- Integration into other medical devices: Other medical device manufacturers will sometimes choose to integrate a prebuilt tablet into their own product. In this role, the tablet serves as the control and user interface for the device.
Considerations When Buying Medical Tablets
So, your healthcare facility has decided they want to add medical-grade tablets to your equipment. Great! But what are the factors you need to consider while choosing a model? The most important aspects of your decision are:
- Cost: This includes the up-front sticker price for the tablets and any expenses that come later down the line for repairing broken units. A tablet with a higher asking price may save money down the line compared to a cheaper model that has to be constantly replaced.
- Training and user adoption: Given the pace of hospital operations, you can't afford to spend much time on training and orientation with your new device. Any new medical tablets will need to be user-friendly and easy to understand.
- Compatibility and integration: Can the tablet interface with the hospital's older legacy equipment for patient care? Can it run the software the hospital uses to manage things like EHRs? These are questions that need to be answered before committing to a model.
- Vendor: Another consideration is choosing to purchase from a reseller or directly from the manufacturer. Say you buy from a reseller and later encounter a technical issue with your tablet. If you send it to the reseller for repairs, they will have to send it to the manufacturer anyway to get it serviced. Cutting out the middleman and buying directly from the source may be better.
- Scalability: Given the size of some healthcare groups, the manufacturer's ability to provide enough devices can be a serious concern. Can the tablet maker provide enough to satisfy your hospital or healthcare group's needs, or will they suffer supply chain issues as they struggle to meet demand?
Industry-Leading Medical-Grade Tablets by Cybernet
In the ever-evolving landscape of healthcare, having the right technology can make all the difference. So whether you're seeking to streamline your clinic's workflows, improve patient outcomes, or simply elevate your healthcare facility, Cybernet's medical tablets are here to lead the way.
Explore our range of medical-grade tablets today and take the first step towards a smarter, more efficient healthcare environment. Get in touch with our experts today — we are more than happy to help you with choosing the right medical tablet for your needs.
Join the conversation and connect with us on this and other relevant topics: Follow us on Facebook, Twitter, and LinkedIn.